Introduction
Footprinting is the process of gathering information about a system, organization, or
individual. Think of it like trying to learn more about a person before meeting them or researching a company
before working with them.In simple terms, footprinting is all about collecting as much data as possible about
the target — including domain names, IP addresses, technologies, and potential vulnerabilities — all without
directly interacting with the target system.This process can include details like domain names, IP addresses,
technologies used, public files, and even employee information. Whether passive or active, footprinting helps
paint a complete picture of the target’s digital presence.In this blog, we’ll explore the types of footprinting, the
tools used by professionals, real-life examples of how it works, and how organizations can protect
themselves from being profiled in this way.
Types of Foot-printing
Foot-printing techniques are generally categorized into two main types:
Passive and Active. Both serve the same goal to gather information but, the way they operate is quite
different.
Active Footprinting
Active footprinting involves direct interaction with the target system to gather
information. This makes it more accurate, but also more likely to be detected by security systems.It requires
direct engagement with the target. Think of it like you check the locks on the doors and windows, among
other potential entry points.

Examples of active reconnaissance activities include:
- Connecting to one of the company servers such as HTTP, FTP, and SMTP.
- Calling the company in an attempt to get information (social engineering).
- Entering company premises pretending to be a repairman.
Examples:
- Ping sweeps.
- Port scanning (Nmap).
- Traceroute.
Risk: This may trigger firewalls or intrusion detection systems (IDS).
Passive Foot-printing
In passive foot-printing, information is collected without directly interacting with
the target system. It’s like quietly observing someone from a distance. The attacker avoids detection because
there is no direct communication with the target. Think of it like you are looking at target territory from afar
without stepping foot on that territory.

Passive reconnaissance activities include:
- Looking up DNS records of a domain from a public DNS server.
- Checking job ads related to the target website.
- Reading news articles about the target company.
Examples:
- WHOIS, lookup.
- Google dorking.
- DNS enumeration.
- Social media investigation.
Popular Foot-printing Tools & What They Do
| Tool Name | Main Purpose |
| whois | Domain registration details |
| nslookup | Dns records resolve |
| dig | Advanced DNS querying tool |
| dnsdumpster | Passive reconnaissance tool |
| sublist3r | Subdomain enumeration tool |
| ffuf | Fuzzing tool — virtual host enumeration |
Lab Environment Setup: To perform hands-on testing of various foot-printing techniques, I used Kali
Linux 2025.2, running inside a VMware Workstation virtual machine. This virtual lab environment allowed
me to safely run reconnaissance tools without affecting any real network.
whois
Purpose:
WHOIS is a passive reconnaissance tool that helps gather publicly available information about a domain. It
reveals important details such as the domain owner, registrar, registration dates, and name servers. Open the
terminal and run the whois tryhackme.com command to get the information.
Command Used: whois tryhackme.com
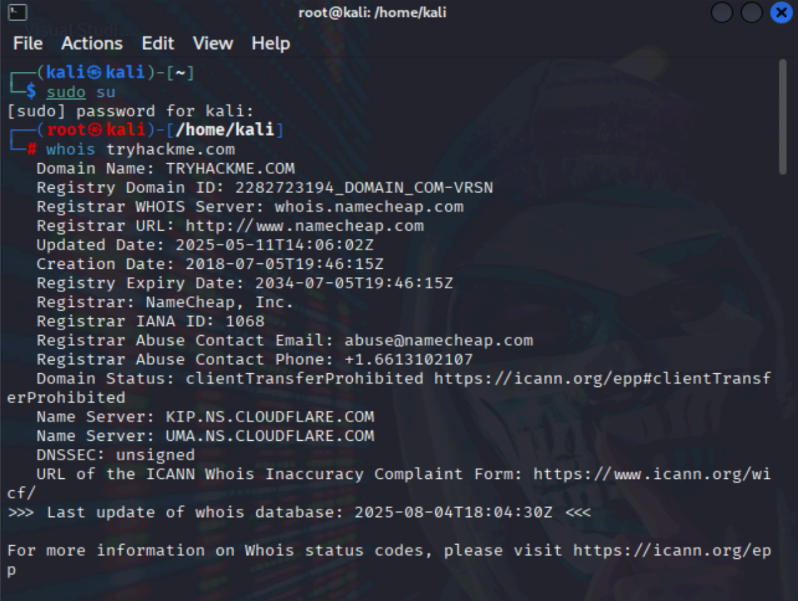
From this WHOIS , we found that tryhackme.com is registered under NameCheap and is using Cloudflare
for its DNS. The domain is secured with a long registration period, indicating long-term intent and stability
Key Insights:
● The domain is active for a long period (16 years: 2018–2034).
● Hosted using Cloudflare name servers (good DDoS protection).
● Registered through NameCheap, a common low-cost registrar.
NSLookup
Purpose: Find the IP address of a domain name using nslookup, which stands for Name Server Look Up.
You need to issue the command nslookup DOMAIN_NAME, for example, nslookup tryhackme.com. Or,
more generally, you can use nslookup OPTIONS DOMAIN_NAME SERVER.
*There are many more public DNS servers that you can choose from if you want alternatives to your ISP’s
DNS servers.
| Query type | Result |
| A | IPV4 Addresses |
| AAAA | IPV6 Addresses |
| CNAME | Canonical Name |
| MX | Mail Servers |
| SOA | Start of Authority |
| TXT | TXT Records |
Command Used:
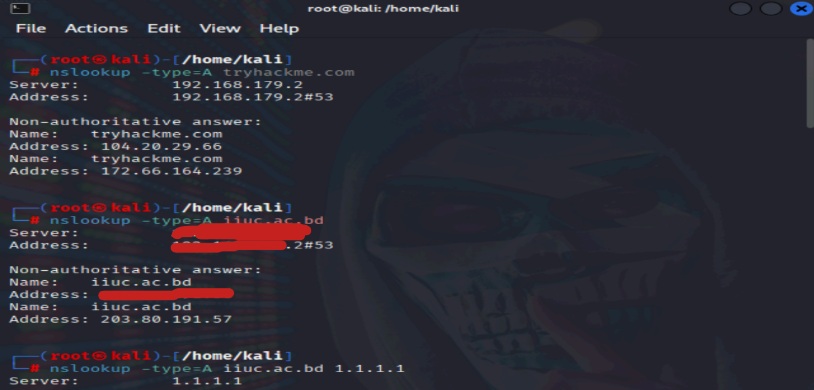
nslookup -type=A tryhackme.com
nslookup -type=A iiuc.ac.bd
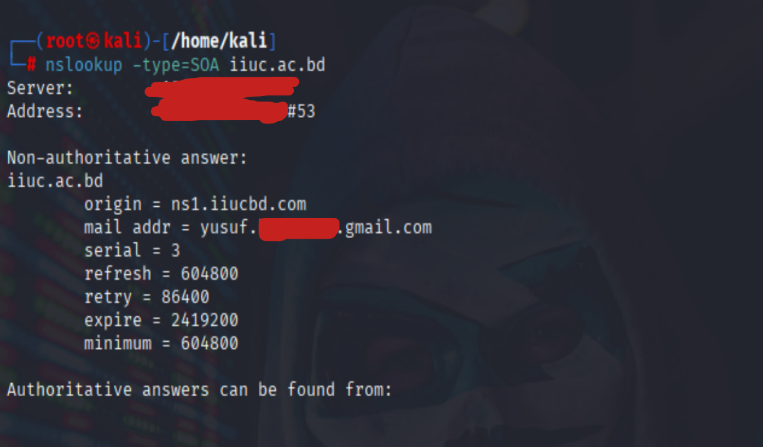
Command Used: nslookup -type=SOA iiuc.ac.bd
Dig
Purpose: For more advanced DNS queries and additional functionality, you can use dig, the acronym for
“Domain Information Groper,” if you are curious. Let’s use dig to look up the MX records and compare them
to nslookup. We can use dig DOMAIN_NAME, but to specify the record type, we would use dig
DOMAIN_NAME TYPE.
Command Used: dig iiuc.ac.bd MX
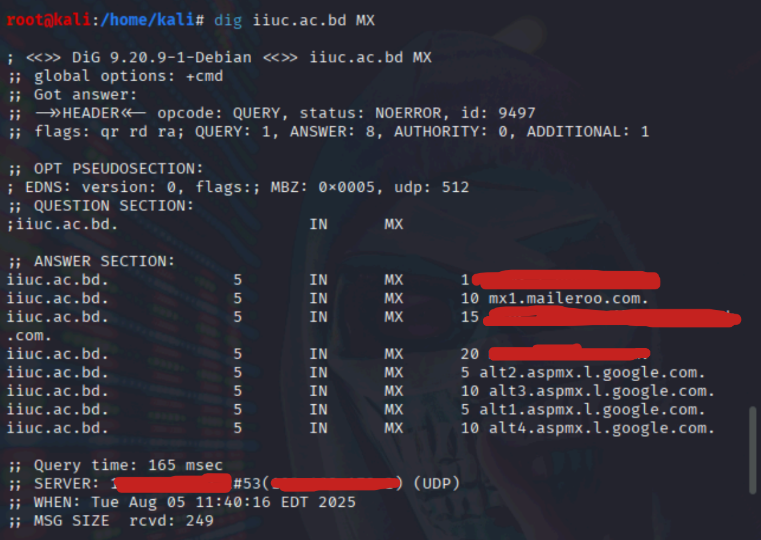
This shows that IIUC uses multiple third-party email providers(Gmail, Outlook, and Maileroo). For a penetration tester or attacker, this could be useful in identifying potential phishing targets.
DNSDumpster
To avoid such a time-consuming search, one can use an online service that offers detailed answers to DNS queries, such as DNSDumpster. If we search DNSDumpster for iiuc.ac.bd, we will discover the subdomain blog iiuc.ac.bd, which a typical DNS query cannot provide. In addition, DNSDumpster will return the collected DNS information in easy-to-read tables and a graph. DNSDumpster will also provide any collected information about listening servers.
Output:
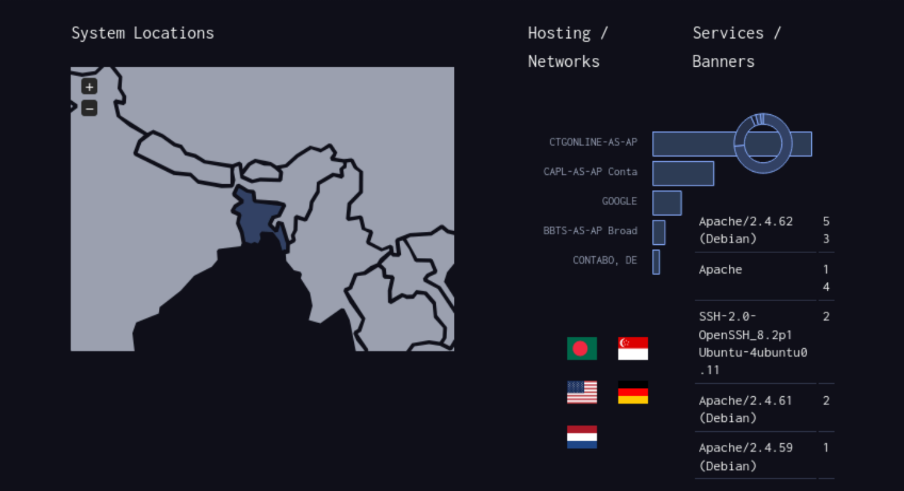
Subdomain Analysis – all.iiuc.ac.bd, cce.iiuc.ac.bd
During the reconnaissance phase, analyzing subdomains can reveal internal systems, exposed services, and even shared infrastructure. Below is a summary of two such subdomains found during A record and service enumeration.
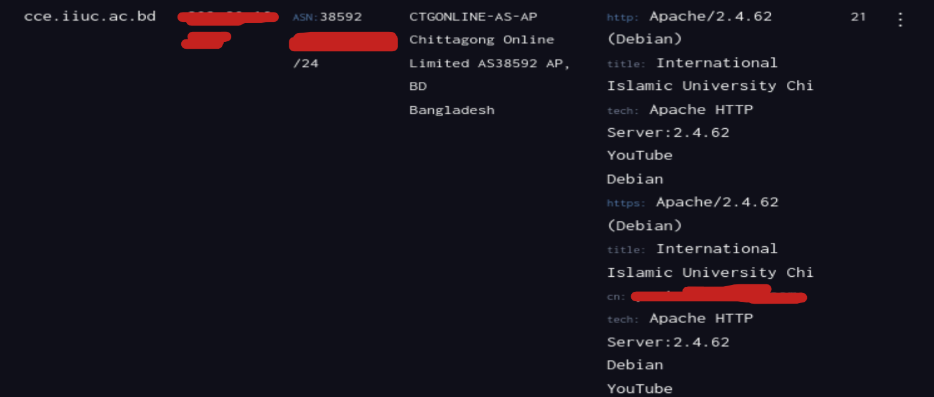
Risk Consideration: Open Apache services with version numbers exposed can be a risk if
unpatched. Reverse DNS revealing portal subdomains can help attackers craft targeted phishing
campaigns or attempt login brute-force on admin portals.
Recommendation: Disable version exposure in HTTP headers.
Shodan.io
Shodan.io tries to connect to every device reachable online to build a search engine of connected “things” in
contrast with a search engine for web pages.Shodan.io collects information related to any device it can find
connected online. Searching for iiuc.ac.bd on Shodan.io will display at least the record shown in the
screenshot above.
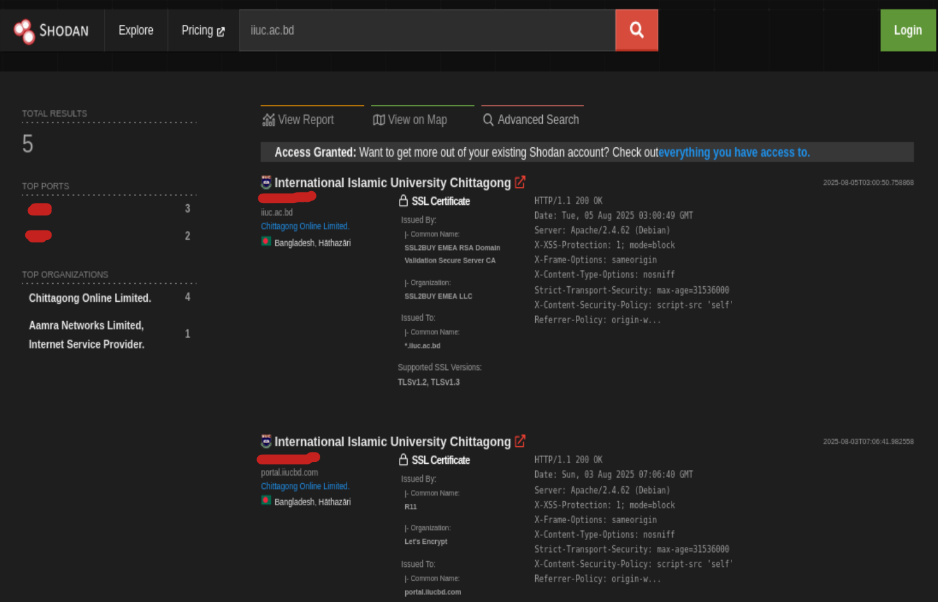
we can learn several things related to our search, such as:
- IP address
- Hosting company
- Geographic location
Sublist3r
Purpose: Sublist3r is an OSINT-based subdomain enumeration tool written in Python. It helps security professionals discover publicly exposed subdomains of a target domain by querying multiple search engines and online resources.
Command used:
apt install sublist3r
sublist3r -d tryhackme.com
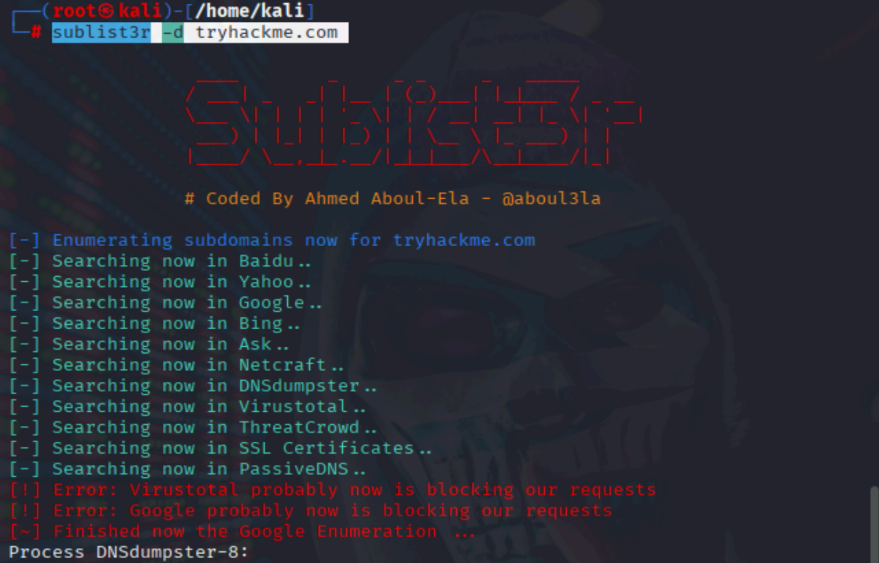
What This Means: Sublist3r helped enumerate multiple live subdomains related to tryhackme.com,
many of which could point to login panels, admin portals. These findings can be further scanned using tools
like nmap, or checked for open directories and version leaks.
Result:
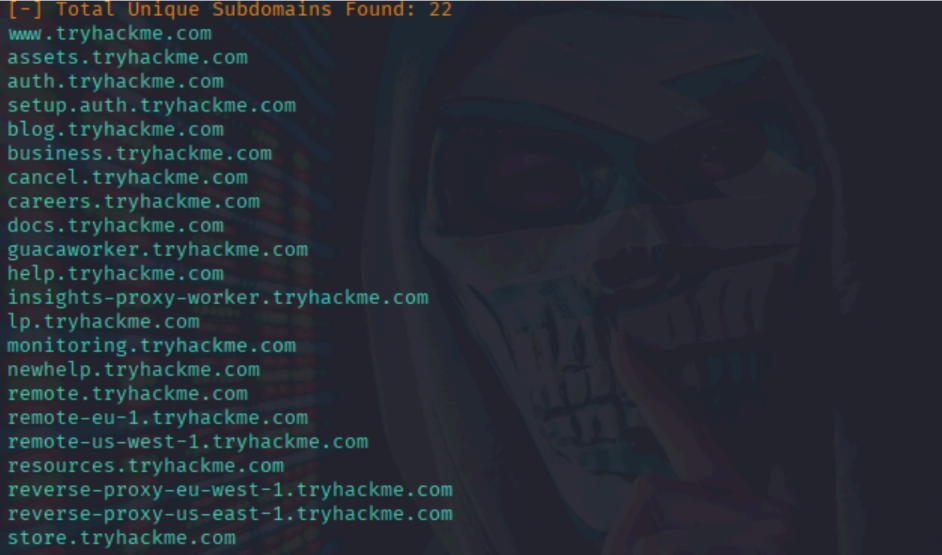
Why Subdomain Enumeration Matters:
- Subdomains often host separate web apps, some outdated or unprotected.
- May lead to indirect entry points into the main infrastructure.
- Helps in surface area mapping before vulnerability scanning.
Summary: Sublist3r is an easy-to-use but powerful tool that speeds up early-stage reconnaissance by
identifying hidden and forgotten web assets of a target organization.
| Ethical Disclaimer!!! The following section discusses the use of FFUF for virtual host enumeration, which involves sending multiple crafted HTTP requests to a web server. This technique can be considered aggressive or intrusive and may trigger security systems like firewalls .This method should only be used in authorized environments, such as your own lab setup, CTF platforms, or with explicit permission from the target. |
Virtual Host Enumeration using FFUF
What is VHost Enumeration?
One Web servers often host multiple websites on the same IP address, known as virtual hosts. Some of
these virtual hosts may not be listed in DNS and are meant to stay hidden. Virtual hosting is a feature that
allows a single web server to host multiple websites and have them appear as if they are hosted on separate,
individual servers.
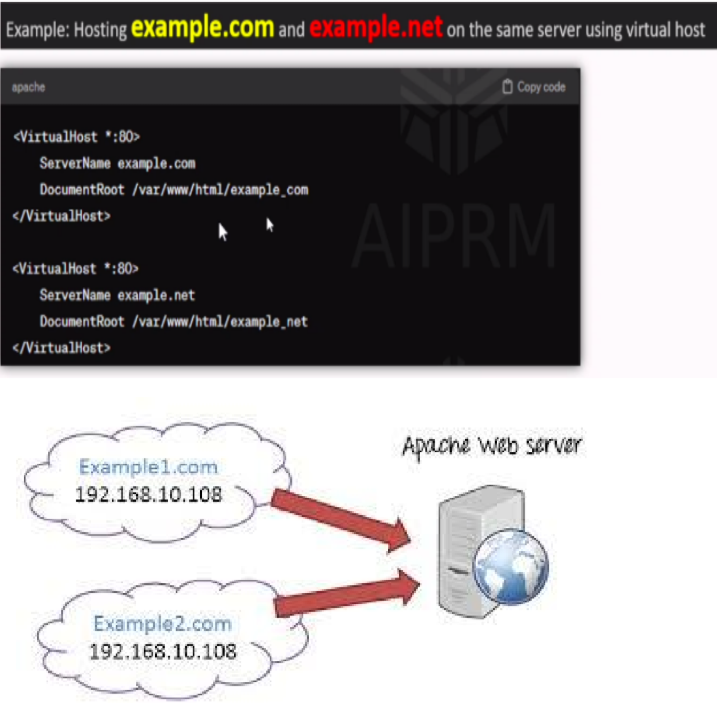
Practical Demonstration: FFUF in Action (TryHackMe Lab)
To show a real-world use case of virtual host enumeration, I used the “TakeOver” room on TryHackMe. This
room focuses on subdomain enumeration, which is perfect for testing FFUF’s capabilities.
Room link : https://tryhackme.com/room/takeover
1st : Connecting TryHackMe server using openvpn.
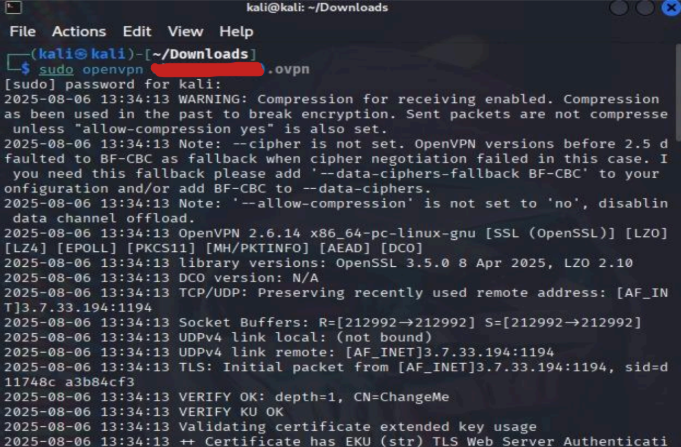
2nd : Join room and copy IP and host name.
3rd : Connect my machine to Tryhackme server.
4th : Then we push Tryhackme room IP and domain name
keyboard :Ctrl-S→ Enter→ ctrl-X → y→ Enter
So we have fully connected our machine.
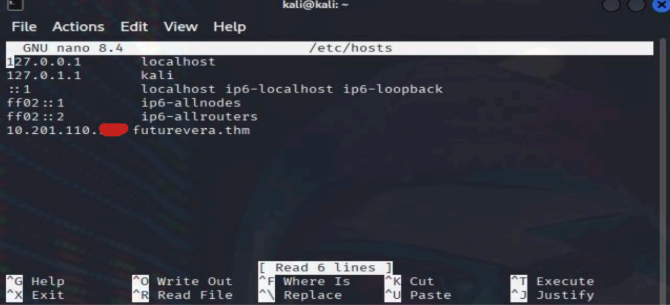
This is our test website for FFUF.
5th : Download the seclist wordlist.
6th : Enter the Command –
Command: ffuf -u https://[IP] -w [WordlistDirectory] -H “HOST:FUZZ.futurevera.thm” -fs 4605 -v -t 10
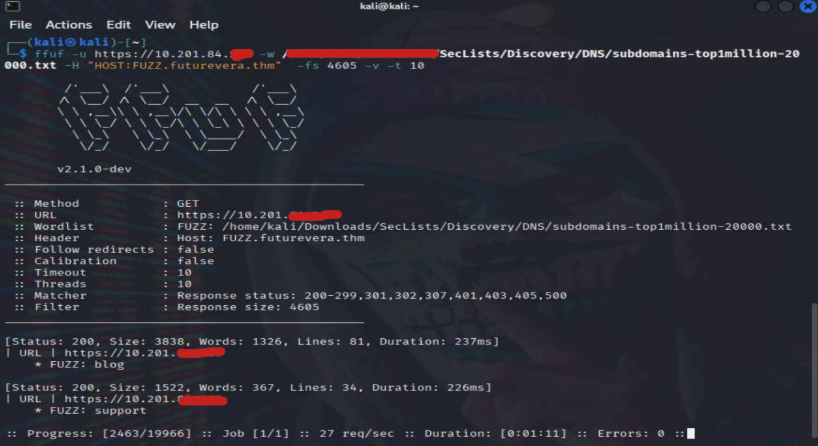
We find the 2 Fuffs : blog, support.
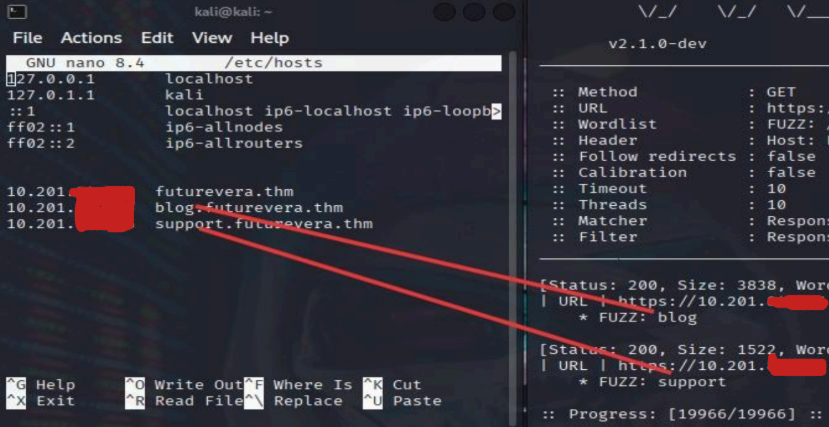
7th : Then we enter support website.
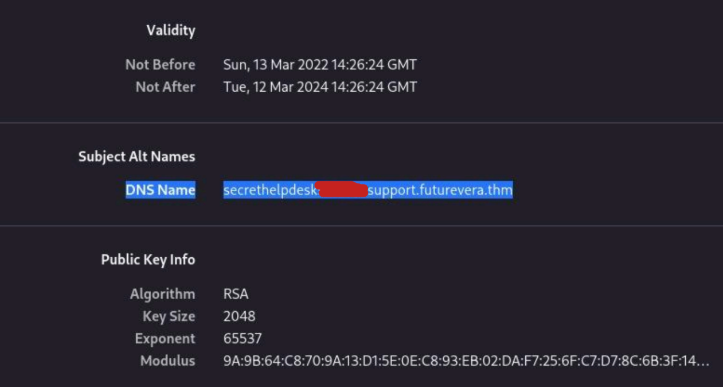
8th : Inspect the certificate to find the DNS name.
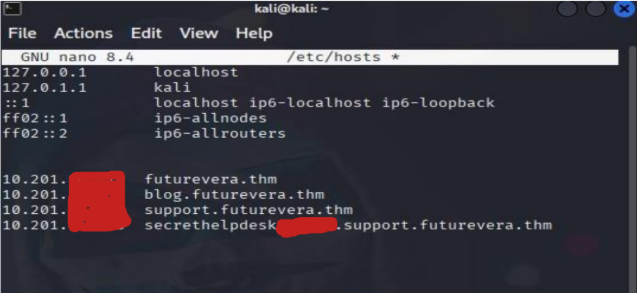
9th : Push the DNS name in host.
10th : Search for it in a browser and find the flag.
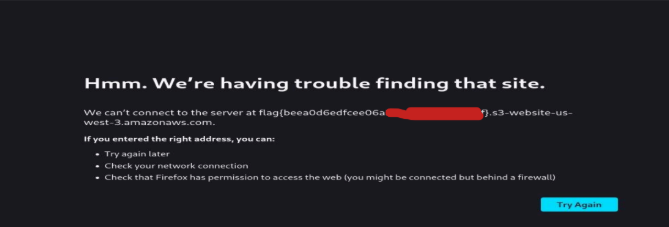
11th : Submit the flag and complete the room.
Summary
As the title suggests, this blog post is entirely dedicated to the first stage of ethical hacking, specifically, Foot-printing and Reconnaissance. The learning outcomes of this blog are both passive and active reconnaissance techniques, alongside the practical lab tasks on Kali Linux.
For passive information gathering, tools such as whois, nslookup, and dig helped us to perform passive enumeration alongside powerful virtual host discovery using ffuf. We introduced information gathering and its types followed with pictures and examples.
The focused coverage of the blog was to demonstrate using multiple tools on actual domains and how cybersecurity experts glean critical information prior to any active assessment. Due to the powerful nature of these tools, together with the risks associated with their use, we highlighted the responsibilities, ethics, and risks of such tools.
For CTF and penetration testing preparations, this blog and its practical insights will be valuable to advanced learners, while also serving to beginners with foot-printing techniques, broadening their scope of reconnaissance.
Disclaimer
This blog does not have any commercial purpose for using iiuc.ac.bd. I have not tried to hack, penetrate, or intrusively access the systems or networks of the institution’s digital infrastructure. Since my intentions for this demo are purely for educational purposes, I would like to demonstrate practical exposure to foot-printing techniques in the context of learning cybersecurity.
Conclusion
Foot-printing is the first step in understanding any target in the cyber world. As we explored tools and techniques from passive lookups to active enumeration, it becomes clear how important this stage is in ethical hacking and penetration testing. With ethical practice and legal boundaries in mind, we can use these techniques to strengthen systems rather than break them.
Acknowledgement
Special thanks to the IIUC Cyber Security Club for arranging this platform to encourage ethical hacking and practical cybersecurity knowledge sharing.

